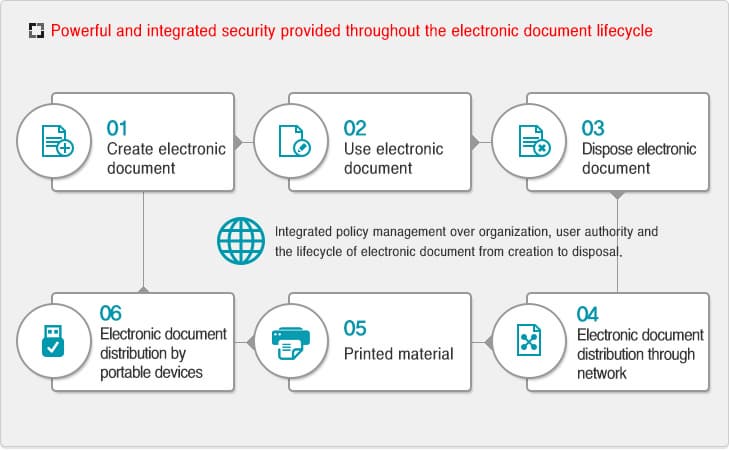
Document Security
Negotiable Min Order Quantity Unit
- Required Quantity
-
- Place of Origin
- South Korea
- Payment Terms
- Negotiable
- Production method
- Negotiable
- Shipping / Lead Time
- Negotiable / Negotiable
- Keyword
- drm, prevent leakage, information security, knowledge asset

SOFTCAMP Co.,LTD.
- Verified Certificate
-
16



| Product name | Document Security | Certification | - |
|---|---|---|---|
| Category |
Computer Software
Computer & Information Technology Service |
Ingredients | - |
| Keyword | drm , prevent leakage , information security , knowledge asset | Unit Size | - |
| Brand name | - | Unit Weigh | - |
| origin | South Korea | Stock | - |
| Supply type | - | HS code | - |
Product Information
Document Security™
Essential information leakage prevention SW solution
│ Description │
Document Security™ DRM solution to prevent corporate confidential information leakage through electronic document encryption, user authentication and user permission control.
│ Business Challenge │
•Steady increase in the use of electronic documents due to digitization of documents and IT advancement
•The confirmed number of illegal technology leakage activities has been showing an upward trend during the last 5 years. These illegal activities are spreading to all of world’s major industries including automobile, shipbuilding and steel etc.
•As cooperative work became essential to the business environment, the potential leakage channels and entities have diversified. Consequently, internal information leakage became more difficult to control.
│ Applications │
•Appropriate for companies and organizations holding confidential information where leakage of such information could lead to great damage
•Appropriate for companies and organizations that engage in frequent cooperation with external entities where security is essential
•Appropriate for companies and organizations that utilize centralized information management systems such as KMS, ERP, CRM and EDMS
•Appropriate for companies and organizations that must conform to information protection regulations such as personal information protection act, the electronic financial transaction act etc.
│ Key Features │
| File and folder encryption Supports mandatory (automatic) encryption, folder encryption and simple encryption functions according to security policy |
|
| Document utilization permission control Control over document usage – read (# of allowed reading), edit, print (# of allowed printing) and decryption Setting different permissions by user/ group and according to document class |
|
| Offline login functions Supports operational continuity while maintaining security Supports encryption/decryption and usage authority control under special occasions, such as business trips or home working, where access to document security management server is not available Transmits the offline usage log history to management server and automatically switches to online status at the point of return to the company |
|
|
Link with work system Provides encryption/ decryption API for a link with work system within an organization, such as groupware, electronic approval, knowledge management (KMS) and ERP system |
| Creating secure file for external transmission Supports safe document distribution in cooperation environment Supports authentication and creation of exe file with usage authority in environment where document security is not installed |
|
| Integrated record management Supports viewing & recording behaviors of users and administrator |
|
| Management efficiency based on hierarchical management system Provides intermediate and lower-level security manager function for increased operational efficiency |
│ Optional Packages │
*Document Security PC DRM
*Document Security Server DRM
*Document Security for MAC Viewer
*Secure Web
*Secure Device
*Secure Laptop
*Cloud DRM
*Document Security for Mobile Viewer
│ Customer Benefits │
| Establishing integrated internal information leakage prevention system Provides integrated information leakage prevention system through laptop computer carrying-in/ out control, selective control of document usage by online/ offline distribution channel and blocking of important information asset leakage (file and webpage) |
|
| Ensuring confidentiality and usability of corporate information assets Ensures confidentiality and security standard compliance for files created and stored in user’s PC |
|
| Ensuring excellent security Powerful encryption function with AES 128bit encryption algorithm Designation as national encrypted product (verification completed, mounted with encryption module), Good Software certification |
|
|
Strengthening work productivity Detailed control of permission by department/ user according to work characteristics and offline login function Provides secure environment as a whole through a link with DLP product |
|
Centralized management Sets and manages permission by user/ group based on roles and document class Enables identification and follow-up inspection on the statue of document usage based on the records of usage |
|
Safe cooperation environment In addition to document distribution between users in an organization, safe file distribution system is provided to external partners. General/ secure documents are safely delivered to outside users for which client is not installed. Controls various document usage permissions, such as in terms of reading count, printing (printing count), editing and period of use |
B2B Trade
| Price (FOB) | Negotiable | transportation | - |
|---|---|---|---|
| MOQ | Negotiable | Leadtime | Negotiable |
| Payment Options | Negotiable | Shipping time | Negotiable |

- President
- Hwan Kuk, Bae
- Address
- 828-7, Yeoksam-dong, Gangnam-gu, Seoul, 135-080 KOREA
- Product Category
- Agency Services,Computer & Information Technology Service,Computer & Software Agents,Computer Software
- Year Established
- 1999
- No. of Total Employees
- 101-500
- Company introduction
-
SoftCamp products are currently used by approximately 300 clients including big major corporations in the world, financial companies, public agencies, etc.
Also, SoftCamp has a fairly high market share in Japan’s security market.
- Main Markets
-
 China
China
 Japan
Japan
 South Korea
South Korea
 Taiwan
Taiwan
- Main Product
Related Products

Alldata 10.53 Mitchell ondemand 5 5.8 Autodata ETKA 7.4

RIMETALK - Enterprise Mobile Application with PTT function
activation and cracked GM GDS2 Tech2win software for GM MD
3d lenticular software, lenticular software free download, 3d lenticular printing software

3D SPECTAT